India made news recently with the revelation that it tops Facebook’s Bug Bounty program with Rs 4.84 crore given to Indian researchers for the job. But what process goes on behind the decisions of how much to pay whom?
Let’s start with some stats.
Inception of the Bug Bounty program by Facebook: 2011
Number of countries involved: 127
Number of Indian researchers and white hat hackers to have received bounties: 205
Total bounty paid to Indians: Rs 4.84 crore
India’s ranks in terms of number of researchers and amount of bounties: #1 and #1
These numbers were calculated since 2011 which is when the Bug Bounty program was launched by Facebook. The programme invites white hat hackers to report security vulnerabilities in Facebook, Instagram, Free Basics , Onavo and Oculus.
Surprising, eh? Not really, India can conveniently be trusted with the world’s worth of tech issues. It’s the home of “techies”, after all.
“Facebook receives more and more high-impact hugs from India each year, reflecting the growing sophistication and technical capabilities of the country’s engineering schools and cyber security programmes,” Adam Ruddermann, technical manager at the program said.
Well, why not? Twenty two year-old Anand Prakash, an Indian security researcher rose to limelight with Facebook awarding him a bounty $15,000 for reporting a Password Reset Vulnerability that let him hack any user’s account by resetting its password via endless brute force of a six-digit code.
The highest bounty paid till date graces the pockets of a Brazilian hacker who managed to hack into Facebook’s server using a remote-code execution vulnerability, with a whopping $33,500.
But how does Facebook decide on the amount?
The website The Hacker News (http://thehackernews.com/2016/03/facebook-bug-bounties.html) reports:
Step 1: The Facebook Bug Bounty team first assesses the potential impact of a reported vulnerability.
Step 2: The difficulty of exploiting a vulnerability is calculated by engineers at Facebook, they check whether it’s high-severity, as well as as well as what a successful attack would require in terms of resources or technical skills.
Step 3: The team then looks at whether any existing features can already reduce the issue, for example, if rate-limiting mechanism can be used to prevent brute-force attacks.
Step 4: Sometimes the reported bugs are actually Facebook features designed to provide users a smoother experience on the social media platform, and are considered less eligible unless absolutely threatening.
These steps are what it takes to decide the base payout for every report.
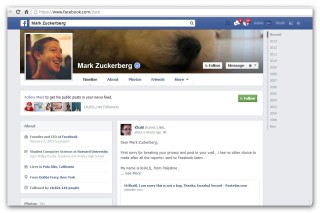
This explains why the bounty evaded Khalil Shreateh from Palestine, who posted details of vulnerability on Mark Zuckerberg’s timeline to prove his point after Facebook Security Team failed to recognise his report thrice.
Despite the widespread attention, Khalil received no bounty since he did not follow the disclosure guidelines correctly and for failing to clarify the vulnerability details to Facebook Security Team.
Quick tip from Facebook:
“The most important factor for getting the maximum bounty possible is to focus on high-risk vulnerabilities, specifically those with widespread impact. So, if you’re looking to maximize your bounties, focus on quality over quantity.”
May the bounty be ever in your favour!